Quick Summary
This article reviews seven leading B2B fraud detection tools across key categories: email security, vendor onboarding, payment verification, and AP fraud detection. But with 70% of fraud incidents now spanning multiple systems, many of these point solutions alone are not enough to stop multi-stage payment fraud.
That’s why we also examine holistic tools, like Trustmi’s end-to-end B2B payment security platform, that address the gaps these point solutions leave behind.
Looking for the Right B2B Fraud Prevention Solution?
With 79% of organizations falling victim to payment fraud in 2024, the question isn’t whether you need fraud detection tools; it’s which combination of categories provides the right coverage for your organization.
Unlike consumer fraud, B2B payment fraud is sophisticated and multi-stage, exploiting gaps between email, procurement, AP, and payment systems.
This Trustmi article outlines how each of the seven tools fits within the broader fraud-prevention stack and where specialized or end-to-end platforms are needed to close those cross-system gaps.
Why Listen to Us?
At Trustmi, we work with organizations across industries to secure the full payment lifecycle, from vendor onboarding to payment verification and execution.
Our platform has analyzed and protected over $200 billion in business payments, giving us a clear view of how fraud actually happens and which tools cover which parts of the workflow. That experience allows us to objectively break down the true categories behind today’s fraud-prevention tools and explain where each one adds value—and where gaps remain.
What is B2B Fraud Detection Software?
B2B fraud detection software identifies and prevents fraudulent activities targeting business payments and financial transactions. Unlike consumer fraud tools that focus on credit card theft or account takeovers, B2B fraud detection addresses vendor impersonation, invoice manipulation, wire fraud, procurement fraud, and business email compromise (BEC).
Depending on the category, tools may analyze emails, vendor data, invoices, or payment instructions, each covering a different layer of the payment workflow.
Benefits of B2B Fraud Detection Software
These tools offer a range of benefits, stopping malicious emails, preventing unauthorized payments, protecting vendor relationships, reducing financial losses, improving compliance, automating manual verification steps, and detecting increasingly sophisticated social engineering attacks.
But each category delivers these benefits in different parts of the workflow, reinforcing the need to understand what each tool actually protects. Across the different categories, B2B fraud tools can help organizations:
- Prevent Payment Fraud: Stop fraudulent wire transfers, ACH payments, and check fraud before money leaves your account.
- Protect Vendor Relationships: Detect vendor account compromises and impersonation attempts that damage trust and business continuity.
- Reduce Financial Loss: Prevent invoice fraud, duplicate payments, and fraudulent banking detail changes that result in direct financial loss.
- Ensure Compliance: Meet regulatory requirements for payment controls, vendor due diligence, and financial security.
- Eliminate Manual Verification: Automate verification processes like callback procedures and manual banking detail checks that are unreliable and time-consuming.
- Detect Sophisticated Attacks: Identify social engineering tactics like executive impersonation, vendor email compromise (VEC), and deepfake fraud that bypass traditional security.
7 Best B2B Fraud Detection & Prevention Tools
Depending on the category, tools may analyze emails, vendor data, invoices, or payment instructions, each covering a different layer of the payment workflow:
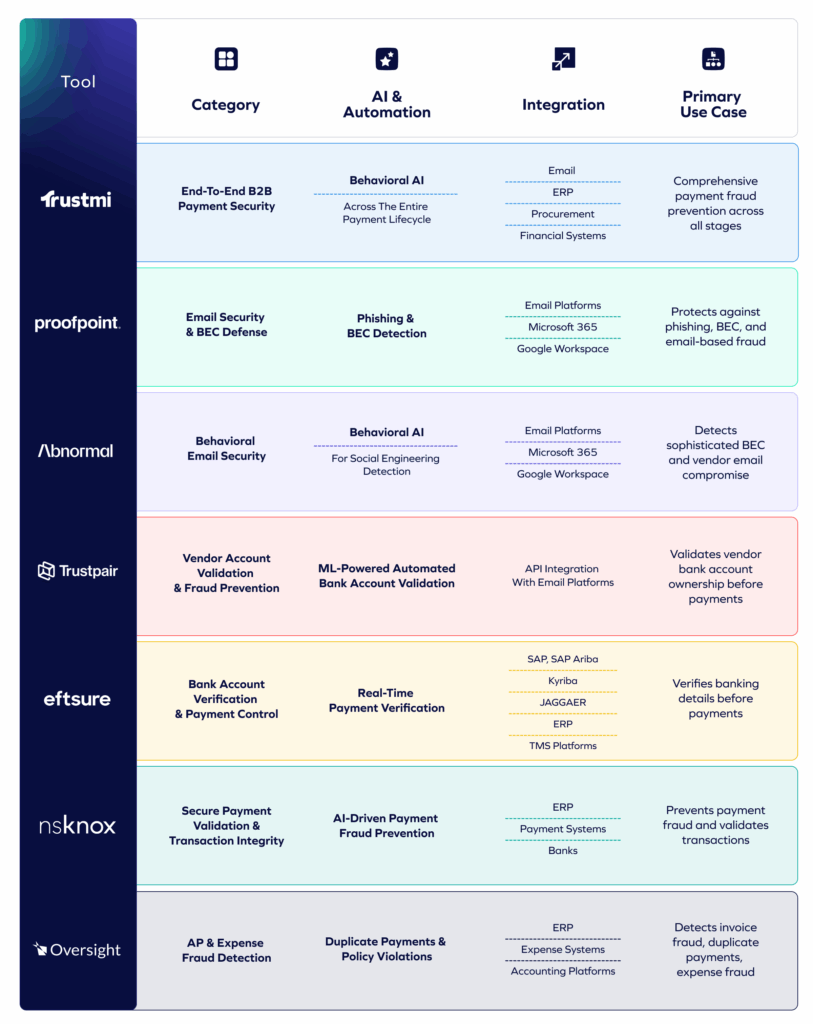
Next, let’s look at each tool in detail.
1. Trustmi: For End-to-End Payment Fraud Protection
Best for: Organizations needing end-to-end B2B payment security across the entire payment lifecycle
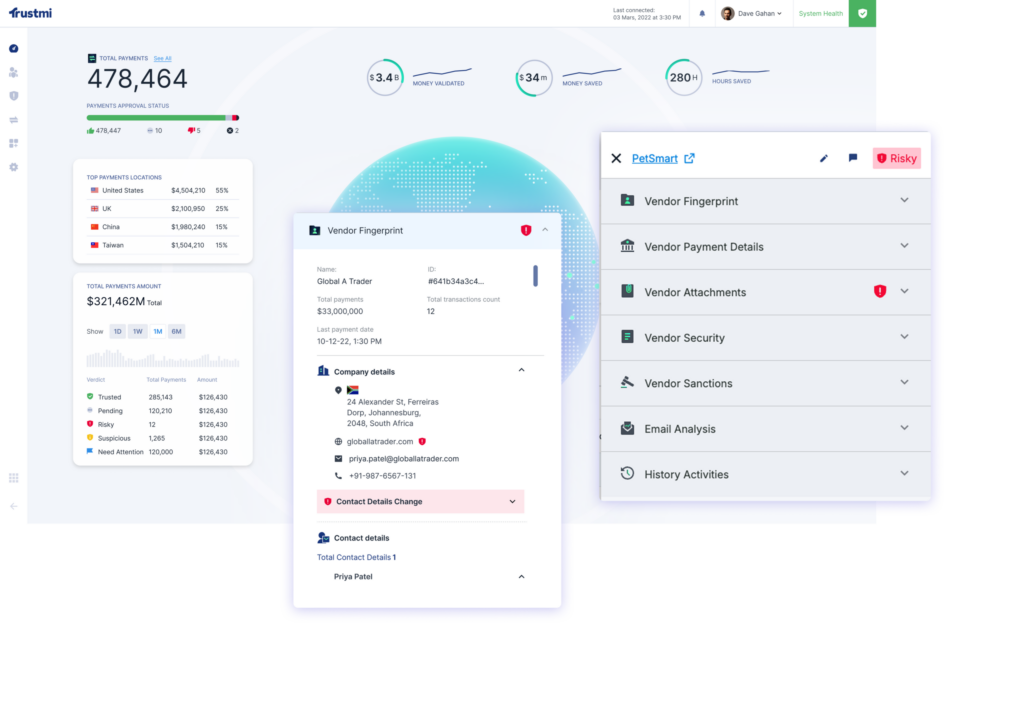
Trustmi is the first comprehensive B2B payment security platform, purpose-built to prevent payment fraud by monitoring and validating every stage from vendor onboarding through payment execution. Unlike point solutions that protect specific stages, Trustmi’s Behavioral AI serves as the connective layer across your email, ERP, procurement, and financial systems to detect sophisticated fraud that other tools miss.
Trustmi provides the cross-system intelligence and automated validation that stops B2B payment fraud, including BEC, vendor impersonation, invoice manipulation, and wire fraud—before money moves.
Key Features
- End-to-End Payment Lifecycle Monitoring: Monitors every stage from vendor onboarding → emails → procurement → invoices → approvals → payments to detect fraud anywhere in the workflow.
- Cross-System Intelligence: Correlates data across email, ERP, vendor records, and payment systems to identify fraud patterns that span multiple tools and security layers.
- Behavioral AI Detection: Learns normal payment patterns, vendor relationships, and transaction behaviors to detect anomalies that indicate fraud, including BEC, vendor impersonation, account takeover, and banking detail changes.
- Financial Context Integration: Understands the financial context of every payment request, correlating it with vendor history, contract terms, and established payment patterns.
- Automated Payment Validation: Automatically verifies every payment against established behavioral patterns, vendor relationships, and banking details before money moves, eliminating manual callbacks.
- Real-Time Fraud Prevention: Stops fraudulent payments instantly across all fraud types: BEC, vendor email compromise, executive impersonation, invoice manipulation, and wire fraud.
Pricing
Trustmi offers tailored pricing based on your business size and needs. Contact Trustmi for a customized quote.
Pros
- Secured over $200 billion in business payments
- End-to-end security across the entire B2B payment lifecycle
- Cross-system intelligence that point solutions can’t provide
- Automates payment validation, eliminating manual verification
- Integrates seamlessly with existing security tools and systems
- Detects sophisticated fraud that bypasses traditional security
Cons
- Requires integration with financial systems for full effectiveness
2. Proofpoint: For Email Protection
Best for: Large enterprises needing comprehensive email threat protection against BEC and phishing

Proofpoint is an enterprise-grade email security solution that defends against phishing, malware, BEC, and other email-based fraud. It protects the communication layer of business payments, using threat intelligence, behavioral analysis, and machine learning to stop fraudulent message and impersonation attempts before they reach employee inboxes.
For B2B fraud prevention, Proofpoint excels at stopping the initial attack vector.
Key Features
- BEC Attack Prevention: Stops over 124 million business email compromise attempts monthly by profiling normal communication patterns and flagging deviations.
- Executive Impersonation Detection: Enforces DMARC, monitors domain lookalikes, and uses advanced forensics to stop spoofing of corporate domains and executive identities.
- Account Takeover Detection: Monitors email and cloud app logins to detect and remediate unauthorized access or hijacked sessions.
- Malicious URL Blocking: Scans URLs in real time to prevent credential theft and malware downloads that enable payment fraud.
- Threat Intelligence Network: Leverages one of the industry’s largest threat intelligence networks to identify emerging B2B fraud tactics.
Pricing
Proofpoint offers customized enterprise pricing based on the number of users and required features. Contact their sales team for a quote.
Pros
- Industry-leading BEC and phishing detection
- Strong executive impersonation protection
- Comprehensive threat intelligence
- Scalable for large enterprises
Cons
- Expensive for smaller organizations
- Complex configuration requires expertise
- Focuses only on email—doesn’t monitor payment workflows
3. Abnormal Security: For Behavioral AI Email Security
Best for: Organizations seeking behavioral AI to detect sophisticated social engineering and vendor email compromise
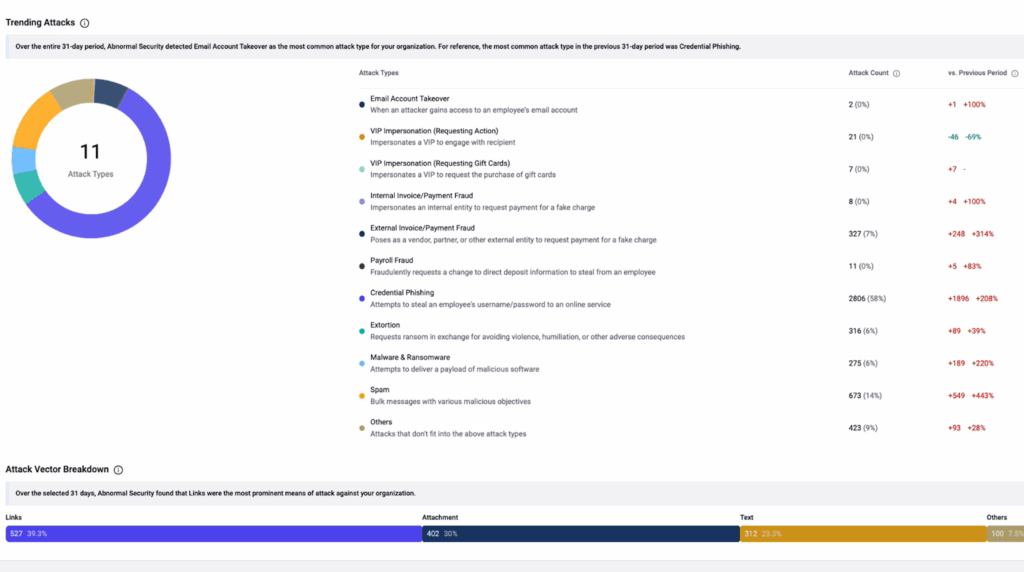
Abnormal Security is a behavioral AI email security platform that learns normal communication patterns to detect anomalies indicative of BEC, vendor email compromise (VEC), and social engineering attacks. Unlike traditional email security that relies on signatures, Abnormal focuses on behavioral analysis to catch attacks targeting payments.
The platform integrates via API with Microsoft 365 and Google Workspace, providing protection without requiring email routing changes.
Key Features
- Behavioral AI Detection: Learns normal communication patterns for employees and vendors to identify social engineering tactics targeting payments.
- Vendor Email Compromise Detection: Analyzes vendor communication patterns to detect compromised vendor accounts requesting payment changes.
- Executive Impersonation Protection: Identifies attempts to impersonate executives or finance team members to authorize fraudulent payments.
- Supply Chain Protection: Monitors vendor relationships and detects anomalies in supplier communications.
- Automated Remediation: Automatically removes malicious emails from inboxes if threats are discovered post-delivery.
Pricing
Abnormal Security uses customized enterprise pricing. Contact their sales team for a quote based on your organization’s size and needs.
Pros
- Excellent at detecting social engineering targeting payments
- Behavioral AI reduces false positives
- Easy API-based deployment
- Strong vendor email compromise detection
Cons
- Focuses only on email—doesn’t extend to payment systems
- Performance strongest in Microsoft 365
- Doesn’t validate banking details or payment requests
4. Trustpair: For Vendor Account Validation
Best for: Mid-market to enterprise organizations needing automated global bank account validation and vendor fraud prevention

Trustpair is a vendor account validation platform that automates bank account ownership verification across 190+ countries. It helps organizations prevent vendor fraud by validating that vendor banking details are legitimate and correctly linked to the intended recipient before payments are made.
The platform integrates directly with ERP, TMS, and procurement systems, embedding fraud prevention into existing workflows without adding manual steps.
Key Features
- Automated Bank Account Validation: Validates vendor banking information automatically during onboarding and before payment execution using three-way matching of company ID, bank account, and ownership correlation.
- Global Coverage: Verifies vendor bank accounts across 190+ countries through an extensive network of banking data sources.
- Continuous Vendor Database Monitoring: Monitors vendor master data in real-time, detecting changes and anomalies that may indicate fraud or data manipulation.
- Payment File Analysis: Scans payment files before execution to detect suspicious behaviors and flag at-risk payments.
- Native ERP/TMS Integration: Connects with SAP, SAP Ariba, Kyriba, JAGGAER, Coupa, Ivalua, and other platforms via 20+ native connectors or API.
Pricing
Trustpair offers customized enterprise pricing. Contact Trustpair for a quote based on your organization’s size and transaction volume.
Pros
- Easy to use with fast validation results
- Strong global coverage across 190+ countries
- 20+ native integrations with major ERP and TMS platforms
- Responsive customer support
Cons
- Occasional false negatives requiring manual follow-up
- Some regional coverage gaps (e.g., Canada)
- Reporting features could be more robust
5. EFTsure: For Payment Verification
Best for: Organizations needing real-time bank account validation before making payments

EFTsure focuses on the final mile of payment execution, validating banking details in real time before funds are released. It prevents payment fraud by verifying that banking details match registered vendor information and flagging suspicious changes to account details.
EFTsure provides the critical last line of defense—ensuring payments go to legitimate accounts even if earlier fraud detection layers are bypassed.
Key Features
- Real-Time Bank Account Validation: Verifies banking details against registered vendor information before payments are released.
- Payment Change Detection: Flags suspicious changes to vendor banking details that may indicate account compromise.
- Vendor Data Cleansing: Validates and cleans existing vendor master data to remove fraudulent or duplicate accounts.
- Payment Verification Network: Leverages a network of verified banking details to identify fraudulent accounts.
- Integration with Payment Systems: Connects with ERPs and payment platforms to validate transactions at the point of payment.
Pricing
EFTsure offers customized pricing based on transaction volume and organization size. Contact EFTsure for a quote.
Pros
- Prevents payment fraud at the critical final step
- Real-time validation before money moves
- Detects suspicious banking detail changes
- Integrates with major ERPs
Cons
- Focuses only on bank account validation
- Doesn’t detect fraud earlier in the payment workflow
- Limited protection against invoice manipulation
6. nsKnox: For Payment Security
Best for: Enterprises seeking comprehensive payment fraud prevention with automated validation
nsKnox provides payment security through automated validation of payment instructions, beneficiary details, and transaction data. It provides a secure payment network that validates transactions before execution.
nsKnox bridges the gap between email security and payment execution, validating payment requests against established patterns and verified beneficiary information.
Key Features
- Automated Payment Validation: Validates every payment against registered beneficiaries and established payment patterns.
- Beneficiary Account Validation: Verifies beneficiary banking details through multiple data sources before payments.
- Payment Pattern Analysis: Analyzes payment history to detect anomalies indicating fraud attempts.
- Secure Payment Network: Provides a trusted network for validating beneficiary information across organizations.
- Real-Time Fraud Detection: Detects and blocks fraudulent payments before money moves.
Pricing
nsKnox offers customized enterprise pricing. Contact nsKnox for specific pricing information.
Pros
- Comprehensive payment validation
- Automated beneficiary verification
- Real-time fraud detection
- Prevents multiple types of payment fraud
Cons
- Focuses on payment execution stage
- Limited visibility into earlier stages (email, procurement)
- Requires integration with financial systems
7. Oversight: For AP Fraud Detection
Best for: Organizations needing to detect invoice fraud, duplicate payments, and expense fraud
Oversight is an AI-powered platform focused on post-payment and accounts payable stages. It detects fraud and policy violations by identifying duplicate invoices, fraudulent expense claims, policy violations, and suspicious payment patterns that indicate fraud.
For B2B fraud prevention, Oversight provides critical visibility into invoice processing and expense management—common targets for fraud schemes.
Key Features
- Duplicate Payment Detection: Identifies duplicate invoices and payments that result in overpayment or fraud.
- Invoice Fraud Detection: Analyzes invoice patterns to detect fraudulent or manipulated invoices.
- Expense Fraud Prevention: Identifies fraudulent expense claims and policy violations in employee expenses.
- Vendor Master File Analysis: Detects suspicious vendor accounts and duplicate vendor records.
- AI-Powered Analytics: Uses machine learning to detect anomalies and fraud patterns in financial data.
Pricing
Oversight offers customized pricing based on organization size and transaction volume. Contact Oversight for a quote.
Pros
- Strong duplicate payment detection
- Comprehensive AP and expense fraud detection
- AI-powered anomaly detection
- Integrates with major ERP systems
Cons
- Focuses on invoice/expense fraud, not payment fraud
- Limited protection against wire fraud or BEC
- Doesn’t validate banking details
Why Point Solutions Aren’t Enough for B2B Payment Fraud
The tools reviewed above (tools 2-7) provide essential protection at specific stages of the payment process. Email security solutions block phishing and BEC attempts. Procurement tools strengthen vendor onboarding. AP analytics platforms catch duplicate invoices and suspicious expenses. Payment-verification tools validate banking details before funds are released.
But here’s the challenge: B2B payment fraud doesn’t happen in just one stage—it exploits the gaps between your security tools and financial controls.
This means point solutions, while essential, leave gaps between email, procurement, AP, and payment systems that attackers exploit. A holistic, payment-lifecycle platform is required to close these gaps and provide true end-to-end protection.
Modern payment fraud attacks are sophisticated and multi-stage:
- The fraud evolves across your payment workflow. Attackers don’t just send a phishing email or submit a fake invoice. Today, 70% of fraud incidents now span multiple systems. They compromise a vendor account through phishing, then manipulate invoice data in your ERP, then change banking details at payment time—moving through multiple systems and security layers.
- Point solutions lack cross-system visibility. Email security can’t see what happens in your ERP. Procurement tools can’t validate banking details. Payment verification tools can’t detect compromised vendor emails. Each tool protects its domain but misses fraud that spans multiple systems. For example, only 27% of organizations said their finance and security teams always have visibility into each other’s fraud incidents.
- Manual processes create vulnerability. Even with multiple security tools, organizations still rely on manual callbacks, email confirmations, and spot-checks to verify payments: processes that are slow, unreliable, and easily manipulated by social engineering. According to a recent survey, manual verification was among the most common fraud controls in use (64%)—yet also the among the most frequently reported to have failed (27.9%).
Protect Your B2B Payments from End to End
The tools reviewed in this guide—Proofpoint, Abnormal Security, Trustpair, EFTsure, nsKnox, and Oversight—provide valuable protection at specific stages of the payment process. Each has its strengths in email security, procurement fraud, payment verification, or invoice fraud detection.
But preventing modern, cross-system B2B payment fraud requires more than individual point solutions. Organizations need end-to-end visibility, cross-system intelligence, and automated validation across their entire payment lifecycle.
Platforms like Trustmi deliver that holistic coverage while complementing the category-specific tools already in your stack to stop sophisticated payment fraud before money moves.Request a demo today to see how Trustmi provides end-to-end B2B payment security.











