Similar to last year, 79% of organizations experienced actual or attempted payment fraud in 2025. The headline number looks steady, right? But the story beneath it isn’t.
As we head into AFP’s annual event in Boston, it’s worth taking another look at the 2025 Payments Fraud and Control Survey—because what appears consistent on the surface is shifting underneath.
AFP’s report suggests why: the threat is shifting from checks and email scams to faster, higher-value attacks that target wires, vendors, and third parties. Once money moves in these channels, it’s almost impossible to get it back.
In Boston, it’s time to ask a harder question: are our existing financial controls truly built for where payment fraud 2025 is heading next?

BEC Is Still the #1 Threat—But It’s Evolving
The AFP report shows that in 2018, 80% of companies reported experiencing Business Email Compromise (BEC). Today, that number has dropped to 63%. And that number has now held steady at 63% for two years. At first glance, that looks like progress, but the data tells a more complex story.
Other, more advanced forms of BEC are accelerating:
- Vendor impersonation fraud rose from 34% to 45%
- Invoice fraud climbed from 14% to 24%
- Third-party compromise increased from 9% to 12%
Why It Matters
What’s on the rise isn’t the CEO-impersonation or phishing scams most people associate with BEC. Instead of attacking your company’s inbox, attackers are targeting your vendors’ inboxes.
These BEC vendor-based compromises use real accounts, legitimate threads, and authentic documentation to insert fraudulent payment instructions—proof that the threat hasn’t disappeared, only evolved.
Which raises an important question: are our current BEC defenses built for this shift?
The Controls in Question: BEC Security
While the overall attacks are consistent, the evolution of the types of BEC attacks exposes a false sense of coverage across teams.
Finance often assumes that “BEC” is a security problem—something handled by phishing filters, awareness training, or secure email gateways. But today’s attacks don’t trigger those defenses.
- Vendor impersonation fraud often originates from compromised or closely spoofed vendor accounts. The emails come from trusted domains or legitimate-looking lookalikes, passing the authentication checks email security relies on.
- Invoice fraud builds on that deception by inserting or altering payment details in real invoices. The purchase data, timing, and documentation are genuine—only the destination account has changed.
- Third-party compromise goes a step further: attackers gain access to a vendor or partner’s actual mailbox, embedding themselves in active conversations and issuing instructions from legitimate domains and addresses.
In each case, the communication appears fully legitimate, which is why phishing filters, training, and gateway defenses rarely flag it.
Email security performs exactly as designed: it stops spam and spoofing, but it cannot detect process-level deception. And because finance believes the threat is already “handled,” these evolving attacks often slip through unnoticed and unowned.
Trustmi Insights
Our own 2025 Socially Engineered Fraud & Risk Report helps explain why these evolving BEC attacks continue to succeed.
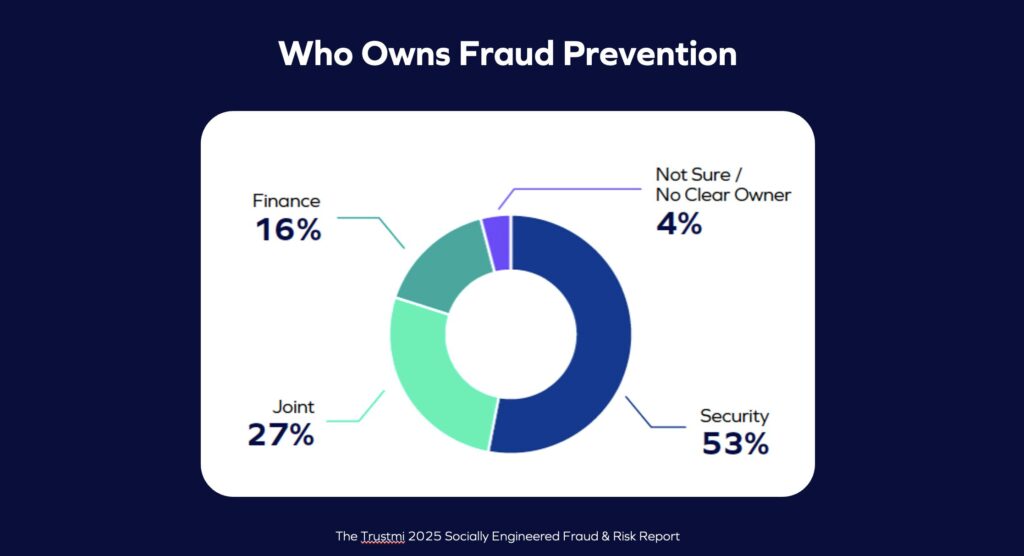
- Ownership remains unclear. Only 27% of enterprises said fraud prevention is a shared responsibility between finance and security. Most still treat BEC as a security issue, assuming phishing filters and training will catch it while finance assumes the threat has been handled upstream.
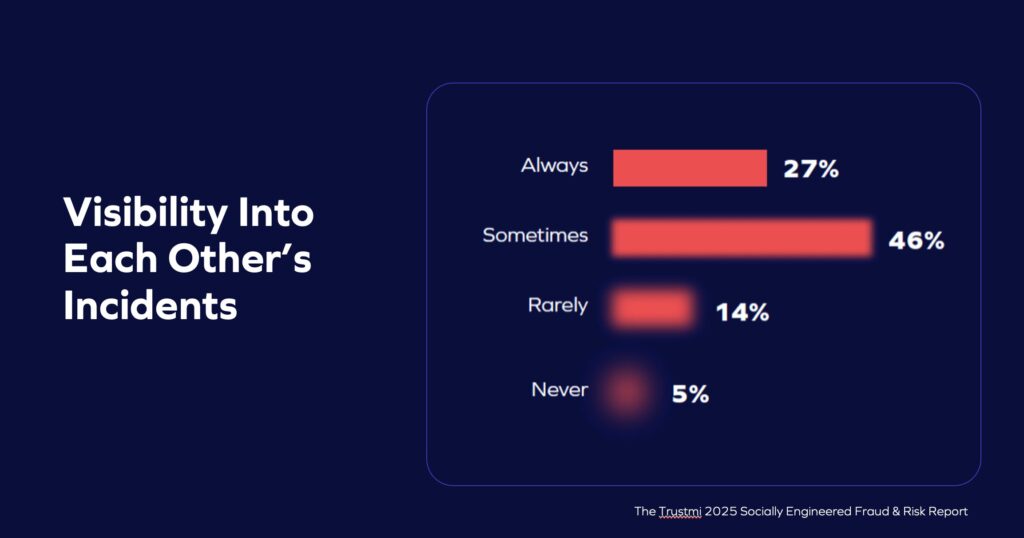
- Visibility breaks down at the handoff. Just one in four leaders said they always have visibility into the other team’s investigations. When context stops at the departmental line, suspicious patterns discovered by one group rarely inform the controls owned by another.
- Attacks cross both domains. Nearly 70% of fraud attempts spanned multiple systems—from email to ERP to vendor portals and payment platforms. The threat now moves between finance and security, but defenses remain confined to one.
The result: attacks thrive in the space between systems and teams, where ownership fades and no single control sees the full picture.
AFP Boston 2025 Question
As we gather in Boston, this ownership gap raises a simple but critical question:
How do we defend against these evolving, third-party attacks?
Wires Are the New Weak Link
Wire transfers have become the top target for payment fraud. According to AFP, 63% of organizations now identify wires as the primary payment method targeted in BEC schemes—up sharply from 39% in 2023. Check fraud remains common at the same rate, but wire fraud is rising faster because these payments are higher-value, faster, and nearly impossible to reverse.
Once the funds move, recovery is rare. Only 22% of organizations recovered more than 75% of stolen funds in 2024, down from 41% the year before. Once money moves through high-speed payment rails, the trail can go cold within hours.
Why It Matters
When an attacker compromises a vendor or alters a payment request, the wire transfer is where the deception becomes hardest to trace and hardest to undo. By that point, every upstream control—approvals, validations, vendor checks—has already cleared the transaction.
Generative AI is making these scams even more convincing, helping attackers mimic vendor language, timing, and documentation with precision. The question now is, what controls can still catch fraud once it reaches this stage?
The Controls in Question: Call Backs & Bank Verification
When it comes to wire payments, finance teams rely on a familiar set of controls—callbacks, bank validations, vendor checks, dual approvals, and payment thresholds—and for good reason. These safeguards are designed to ensure that payments meet policy requirements, confirm routing data, and provide an audit trail for compliance.
But there’s a critical gap. These controls confirm that a payment matched an approved invoice or that an approver signed off, but they don’t verify who actually owns the receiving account—or whether the request itself has been manipulated.
In other words, these defenses are built for accuracy, not authenticity. They ensure the process is followed, not that the process hasn’t been compromised.
- Callbacks confirm a change with a “known” contact, but that contact data may already be compromised.
- Bank validations verify that an account exists, not that it belongs to the correct vendor.
- Dual approvals confirm that a payment was reviewed, but both approvers are often looking at the same falsified record.
Each system signs off on its own step, but none see the full journey. The gap isn’t technical—it’s contextual—and it widens with every new team and system added.
Trustmi’s Insight
Those handoffs matter—and our data shows why.
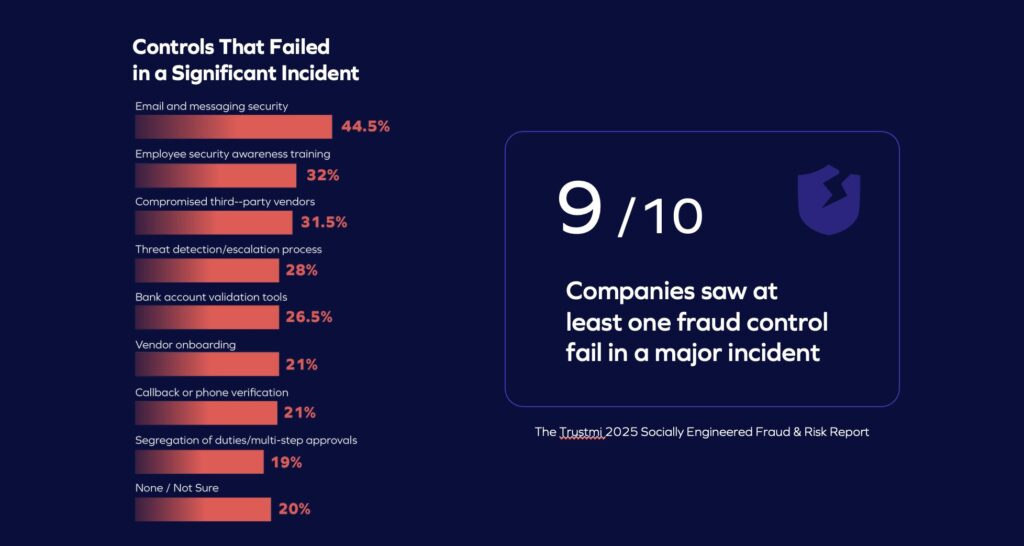
- Nine in ten organizations reported at least one control failure during a major fraud event.
- The most widely used safeguards—email security (44%), training (32%), and callbacks (21%)—were also the ones most often linked to significant incidents.
Every organization follows policy, validates accounts, and logs callbacks, yet the attacks keep getting through. The issue isn’t execution; It’s design. These controls confirm details, not authenticity; process, not context.
Each system signs off on its own step, but none see the whole journey. The gap isn’t technical—it’s contextual. And the more systems and teams involved, the wider that gap becomes.
AFP Boston 2025 Question
The more those silos expand, the easier it becomes for attackers to move unseen. Which leads to an even harder question:
If every control can be fooled by a legitimate-looking request, what will it take to catch fraud in motion?
Big Companies, Bigger Targets
The larger the organization, the more systems, people, and controls are involved, and the more silos take shape. Each team protects its own process, but few see how those processes connect.
That’s why large enterprises, especially those earning over $1B annually, face the highest attack rates across wire, vendor, and invoice fraud. AFP links this to “complex, siloed systems” that expand both vulnerability and response time.
Why It Matters
Most large organizations trust their financial controls. But in big enterprises, process complexity becomes opportunity. The more people, platforms, and partners involved in a transaction, the harder it is to see what’s really happening from start to finish.
Finance, procurement, and security each own part of the process, yet no one owns the full picture. That lack of shared visibility turns scale into surface area, and attackers exploit every gap between teams.
The Controls in Question: Most of Them
Enterprises don’t lack defenses; they have hundreds. But more layers don’t mean more protection. When controls operate independently, they create the fragmentation attackers rely on.
Systems built to enforce compliance end up concealing risk by scattering accountability—especially when finance can’t see across every system that touches a payment.

Trustmi’s Insight
Our 2025 Socially Engineered Fraud & Risk Report found that 34.5% of leaders cited finance–security misalignment as a factor in a recent fraud or near miss.
That’s 1 in 3 companies.
How does this happen? Well, once fraud crosses systems, visibility breaks down. Security focuses on breaches; finance focuses on payments. But modern fraud moves between them—and no one has end-to-end context.
Each team follows policy, but when no one owns the full picture, the payment still goes out. Finance can’t assume traditional controls or adjacent teams will catch these attacks. Protecting payments now means taking ownership of visibility—across systems, processes, and people—before the next request in motion becomes another loss.
AFP Boston 2025 Discussion Prompt
At scale, complexity itself becomes the risk. So the question for finance leaders is clear:
If complexity creates risk, how can finance break the silos that attackers depend on?
The Path Forward for Payment Fraud 2025
As we gather in Boston, the AFP 2025 report offers more than a snapshot of risk—it’s a prompt for change.
Across every system and control, the question is the same: Are we protecting the process, or the payment itself?
- Are today’s controls built to recognize the speed and sophistication of GenAI-powered payment fraud?
- If payment fraud moves between systems, can we still rely on controls that don’t?
- How can we close the silos between teams, systems, and controls to create the context needed to detect modern payment fraud?
We’ll be at AFP Boston, Booth #448, excited to tackle these hard questions. Stop by to continue the conversation, or you can also book a meeting to discuss these findings in more detail.
Safe travels, and we’ll see you in Boston!