Quick Summary
This article reviews six leading B2B account takeover solutions and supporting tools: Proofpoint, Abnormal Security, Coupa, ORO, Microsoft Defender for Office 365, and Okta. Together, they address different parts of the B2B account takeover lifecycle, from identity and email security to vendor account integrity. We also cover Trustmi, the payment fraud prevention platform that provides the critical layer beyond ATO, stopping the financial damage that account takeovers enable.
Looking to Safeguard Your Business from Account Takeovers?
B2B account takeover attacks have become one of the most dangerous threats to business payments. When attackers compromise vendor accounts, employee email credentials, or partner logins, they don’t just steal data—they steal money, customer data, trade secrets, and more.
In this Trustmi article, we explore six B2B account takeover solutions and supporting tools that play key roles in preventing and mitigating account compromise—from email and identity security to vendor account integrity—plus Trustmi’s payment fraud prevention platform that stops the financial damage account takeovers enable.
Why Listen to Us?
At Trustmi, we specialize in protecting businesses from payment fraud that results from account takeovers.

With our AI-driven solutions securing over $200 billion in payments for our clients, we’re uniquely positioned to guide you in selecting the best tools to prevent unauthorized access and safeguard your assets.
What is B2B Account Takeover?
B2B account takeover happens when attackers gain unauthorized access to business accounts such as employee email, vendor portals, cloud applications, or supplier systems. Once inside, they can impersonate trusted users, move laterally, steal data, alter vendor information, or manipulate business processes across finance, operations, and supply chain workflows.
Unlike consumer ATO, which targets personal shopping or banking accounts, B2B account takeover focuses on accounts with operational or financial authority, including access to communication tools, vendor records, and enterprise applications.
B2B account takeover solutions and supporting tools work across different stages of the attack path, from preventing unauthorized access to securing vendor accounts and supplier workflows that attackers often abuse. These capabilities include:
- Multi-factor authentication and adaptive access controls
- Behavioral analysis to detect suspicious login attempts
- Credential theft protection and phishing prevention
- Session monitoring and risk-based authentication
- Identity verification and device trust assessment
Why Account Takeover Solutions Aren’t Enough to Stop Payment Fraud
The B2B account takeover solutions reviewed below offer protection across the identity, email, and vendor layers—but even together, they can’t stop the payment fraud that often follows an account takeover.
Even with the best ATO protection in place, sophisticated payment fraud can still succeed:
- Prevention isn’t always possible. Despite best efforts, some account takeovers will succeed through zero-day exploits, insider threats, or sophisticated social engineering. When they do, attackers move quickly to manipulate payment data.
- ATO tools lack financial context. Access security solutions can’t see what happens in your ERP, procurement systems, or payment workflows. They can’t detect when a legitimate user (using compromised credentials) submits fraudulent banking details or manipulates vendor information.
- The fraud happens after the takeover. By the time attackers are ready to steal money, they’re already past your access controls. The actual fraud occurs during invoice processing, payment approval, or wire transfers (stages that ATO prevention tools don’t monitor).
- Compromised trusted accounts bypass controls. When attackers take over legitimate vendor or employee accounts, their fraudulent payment requests come from “trusted” sources that have already passed authentication.
Trustmi: The Payment Fraud Prevention Layer
Trustmi is the payment fraud prevention platform that protects your money after account takeovers succeed.
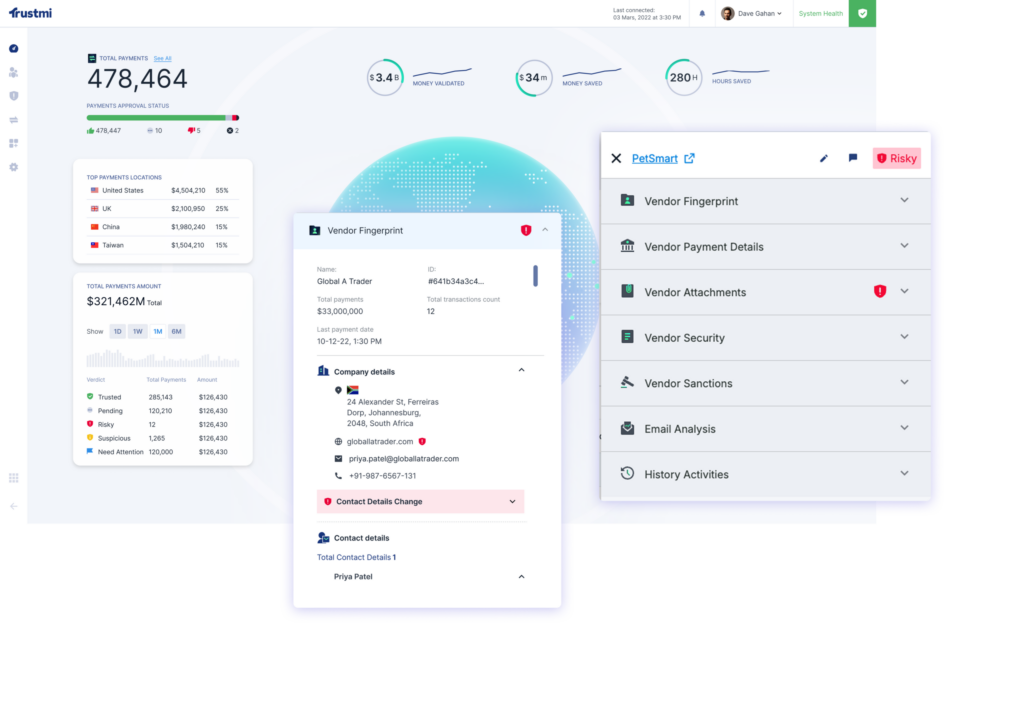
While ATO prevention focuses on stopping unauthorized access, Trustmi secures your entire payment process—monitoring vendor communications, payment workflows, and banking details across your ERP and financial systems.
Trustmi’s Behavioral AI works alongside your ATO prevention tools to address the critical gaps in access-only protection:
- Beyond the access point: Trustmi monitors your entire payment process across ERP, procurement, and financial systems to catch fraud that occurs after attackers gain access through compromised accounts.
- Financial context awareness: Integrates with your payment workflows to detect fraudulent banking details, altered vendor information, and suspicious payment requests that access controls can’t see.
- Behavioral anomaly detection: Learns normal patterns for vendor communications, payment requests, and banking details to flag anomalies that indicate account takeover fraud—even from “legitimate” accounts.
- Real-time payment protection: Validates every payment against established behavioral patterns before money moves, stopping fraud during invoice processing, payment approval, and wire transfers.
6 Top Tools for B2B Account Takeover Prevention
Now let’s explore the leading B2B account takeover solutions and supporting tools that protect different parts of the access layer. Some of these tools prevent direct account takeover (identity and email security), while others secure vendor accounts and supplier data—key targets attackers manipulate after gaining access.
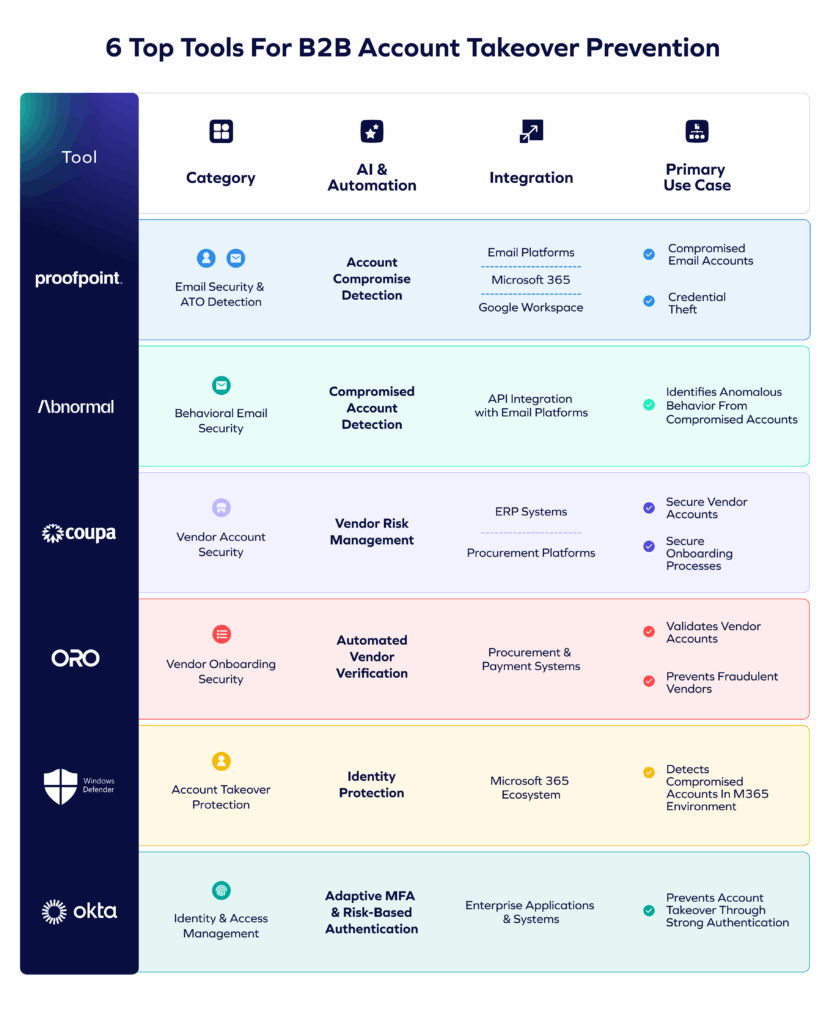
Together, these six tools protect different parts of the access layer, helping reduce the vulnerabilities attackers exploit during B2B account takeovers. Next, let’s look at each in detail.
1. Proofpoint
Best for: Large enterprises needing comprehensive email security with account takeover detection
Proofpoint provides enterprise-grade email security that includes advanced account takeover detection capabilities. It monitors for compromised email accounts, credential theft, and suspicious login activity that could indicate account takeover attempts.
For B2B account takeover prevention, Proofpoint excels at detecting when email accounts have been compromised and stopping attackers from using those accounts to send fraudulent payment requests.
Key Features
- Account Takeover Detection: Monitors email and cloud app logins to detect unauthorized access, credential theft, and hijacked sessions.
- Credential Theft Protection: Prevents phishing attacks and credential harvesting that lead to account takeovers.
- Suspicious Login Monitoring: Analyzes login patterns, device information, and access locations to identify compromised accounts.
- Compromised Account Remediation: Automatically remediates compromised accounts by triggering password resets and blocking suspicious activity.
- User Behavior Analytics: Profiles normal email behavior to detect anomalous activity from potentially compromised accounts.
Pricing
Proofpoint offers customized enterprise pricing based on the number of users and required features. Contact their sales team for a quote.
Pros
- Industry-leading email security and ATO detection
- Strong credential theft protection
- Comprehensive threat intelligence
- Automated remediation for compromised accounts
Cons
- Expensive for smaller organizations
- Complex configuration requires expertise
- Focuses on email—doesn’t protect payment workflows
2. Abnormal Security
Best for: Organizations seeking behavioral AI to detect compromised account activity and vendor email compromise
Abnormal Security uses behavioral AI to detect when accounts have been compromised by analyzing communication patterns and identifying anomalous behavior. Unlike traditional security that looks for malicious content, Abnormal focuses on behavioral anomalies that indicate account takeover.
The platform is particularly effective at detecting vendor email compromise (VEC)—when vendor accounts are taken over and used to send fraudulent payment requests.
Key Features
- Behavioral Anomaly Detection: Learns normal communication patterns for employees and vendors to identify suspicious behavior from compromised accounts.
- Vendor Email Compromise Detection: Detects when vendor accounts are compromised and used to send fraudulent payment requests or banking detail changes.
- Compromised Account Identification: Identifies compromised accounts based on communication anomalies, access patterns, and behavioral changes.
- Post-Delivery Remediation: Automatically removes fraudulent emails sent from compromised accounts even after delivery.
- Account Risk Scoring: Assigns risk scores to accounts based on behavioral patterns to identify high-risk compromised accounts.
Pricing
Abnormal Security uses customized enterprise pricing. Contact their sales team for a quote based on your organization’s size and needs.
Pros
- Excellent at detecting compromised account behavior
- Behavioral AI reduces false positives
- Strong vendor email compromise detection
- Easy API-based deployment
Cons
- Focuses only on email—doesn’t extend to payment systems
- Doesn’t validate banking details or payment requests
- Performance strongest in Microsoft 365
3. Coupa
Best for: Organizations needing vendor account security and supplier risk management
Coupa isn’t an account takeover tool in the traditional identity-security sense. It won’t stop attackers from stealing email credentials or logging into business systems.
However, Coupa does strengthen a critical part of B2B account takeover prevention: the vendor data and supplier workflows attackers commonly exploit after compromising a supplier’s email account.
By enforcing strict controls around vendor identity, onboarding, and changes to supplier information, Coupa reduces the likelihood that a compromised vendor can alter supplier data, submit fraudulent banking details, or slip manipulated information into procurement workflows. These controls directly address the downstream fraud risks that follow a supplier account takeover.
Key Features
- Vendor Account Monitoring: Tracks vendor account access, changes, and activity to detect suspicious behavior.
- Supplier Risk Assessment: Continuously monitors supplier risk indicators including financial health, compliance status, and security posture.
- Secure Vendor Onboarding: Validates vendor information during onboarding to prevent fraudulent vendor accounts.
- Access Controls: Enforces access controls and approval workflows for vendor account changes.
- Supplier Data Management: Maintains secure vendor master data with controls to prevent unauthorized changes.
Pricing
Coupa offers customized pricing based on organization size, transaction volume, and required modules. Contact Coupa for a tailored quote.
Pros
- Comprehensive vendor account visibility
- Strong supplier risk monitoring
- Secure vendor onboarding processes
- Scalable for enterprises
Cons
- Focuses on procurement, not payment execution
- Doesn’t detect compromised email accounts
- Complex implementation for full platform
4. ORO
Best for: Organizations needing automated vendor verification and onboarding security to block fraudulent or fake suppliers

ORO is not an account takeover prevention tool for employee or vendor email accounts. Instead, its focus is on verifying vendor legitimacy and preventing fraudulent vendor profiles from being created—a key stage attackers often target after compromising someone’s credentials.
Within the broader landscape of B2B account takeover prevention, ORO strengthens the vendor layer: ensuring supplier identities, banking details, and onboarding workflows are secure so attackers can’t exploit compromised accounts to introduce fake vendors or alter vendor information.
By validating vendor data at the source and continuously monitoring for suspicious changes, ORO reduces the downstream fraud risk that follows a vendor account takeover.
Key Features
- Automated Vendor Verification: Validates vendor identity, banking details, and business legitimacy during onboarding.
- Vendor Account Validation: Verifies vendor account information against multiple data sources to prevent fraudulent accounts.
- Banking Detail Verification: Confirms vendor banking details match registered business information.
- Ongoing Vendor Monitoring: Continuously monitors vendor accounts for suspicious changes or activity.
- Vendor Risk Scoring: Assigns risk scores to vendor accounts based on verification results and ongoing behavior.
Pricing
ORO offers customized pricing based on organization size and vendor volume. Contact ORO for specific pricing information.
Pros
- Automated vendor verification reduces manual work
- Strong banking detail validation
- Prevents fraudulent vendor accounts
- Ongoing vendor account monitoring
Cons
- Focuses on vendor onboarding stage
- Doesn’t detect compromised employee accounts
- Limited visibility into payment execution
5. Microsoft Defender
Best for: Organizations using Microsoft 365 needing integrated account takeover protection
Microsoft Defender for Office 365 provides comprehensive security for the Microsoft 365 environment, including advanced account takeover protection. It monitors for compromised accounts, suspicious sign-ins, and credential theft within the M365 ecosystem.
For organizations heavily invested in Microsoft 365, Defender provides native account takeover detection that integrates seamlessly with existing Microsoft security tools.
Key Features
- Account Takeover Detection: Monitors for suspicious sign-in attempts, compromised credentials, and account anomalies in Microsoft 365.
- Risk-Based Authentication: Evaluates sign-in risk based on location, device, behavior, and real-time threat intelligence.
- Compromised Account Remediation: Automatically responds to compromised accounts with password resets, session revocations, and access restrictions.
- Credential Theft Prevention: Protects against phishing, malware, and other attacks that steal user credentials.
- Integration with Microsoft Security: Works seamlessly with Microsoft Entra ID (Azure AD), Microsoft Sentinel, and other Microsoft security tools.
Pricing
Microsoft Defender for Office 365 is available in two plans:
- Plan 1: Included in Microsoft 365 Business Premium or available as an add-on
- Plan 2: Advanced protection features, available as an add-on
Contact Microsoft for specific pricing based on your organization’s Microsoft 365 license.
Pros
- Native integration with Microsoft 365
- Automated remediation for compromised accounts
- Strong credential theft protection
- Risk-based authentication
Cons
- Limited to Microsoft 365 environment
- Doesn’t monitor non-Microsoft systems
- Doesn’t protect payment workflows outside M365
6. Okta
Best for: Enterprises needing strong authentication and identity security to prevent account takeovers

Okta provides comprehensive identity and access management (IAM) with advanced authentication controls designed to prevent account takeovers. Through adaptive multi-factor authentication (MFA), risk-based access policies, and continuous authentication, Okta makes it significantly harder for attackers to compromise accounts.
For B2B account takeover prevention, Okta provides the foundational identity security that prevents unauthorized access to business applications and systems.
Key Features
- Adaptive Multi-Factor Authentication: Implements risk-based MFA that adapts authentication requirements based on user behavior, device, location, and risk level.
- Risk-Based Access Policies: Evaluates access requests against risk factors and enforces appropriate authentication or blocks suspicious access attempts.
- Continuous Authentication: Monitors user sessions continuously to detect account takeover during active sessions.
- Device Trust: Verifies device health and trustworthiness before granting access to prevent access from compromised devices.
- Passwordless Authentication: Supports passwordless authentication methods that eliminate credential theft vulnerabilities.
Pricing
Okta offers multiple pricing tiers based on features and user count:
- Workforce Identity Cloud: Custom pricing based on users and features
- Customer Identity Cloud: Custom pricing based on monthly active users
Contact Okta for specific pricing information.
Pros
- Strong authentication prevents account takeovers
- Adaptive MFA balances security and user experience
- Comprehensive identity security platform
- Extensive integration ecosystem
Cons
- Focuses on prevention, not detection of compromised accounts
- Doesn’t monitor payment workflows
- Can be expensive for smaller organizations
Protect Your Business Payments from Account Takeover with Trustmi
We’ve explored six top B2B account takeover solutions and supporting tools—from identity and email security to vendor verification and supplier account integrity. Each plays a different role in reducing the access vulnerabilities attackers exploit during account compromise.
But to stop the payment fraud that account takeovers enable, you need Trustmi’s payment-level protection. Trustmi works alongside your ATO prevention tools to secure the critical payment processes that access controls can’t reach.
Together, account takeover prevention and Trustmi’s payment fraud prevention provide complete protection—from access control to payment security.
Request a demo today and see how Trustmi prevents payment fraud that originates from account takeovers.















