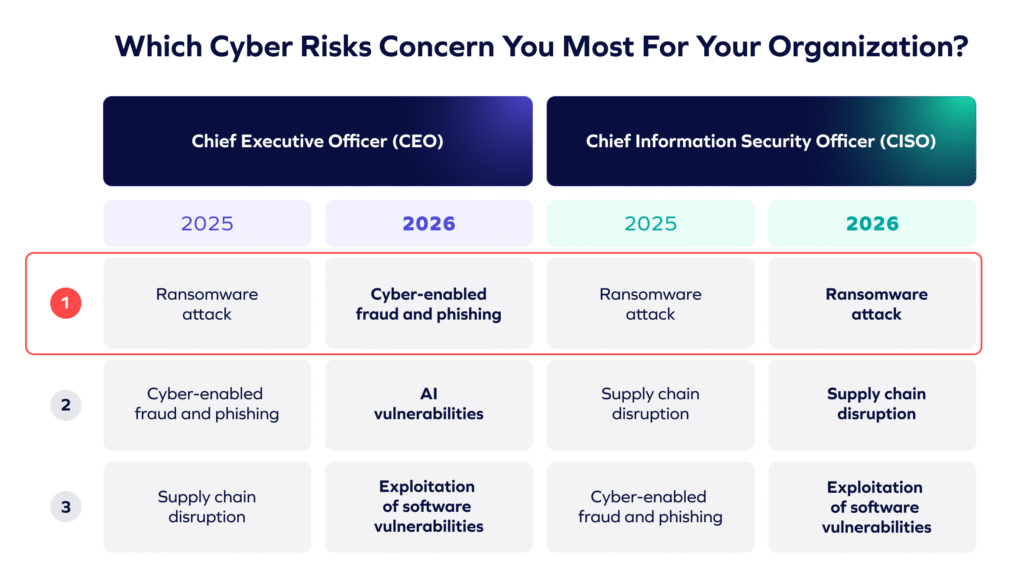
Cyber-enabled fraud has emerged as the top concern for CEOs.
Ransomware remains the primary focus for CISOs.
That gap? It matters. It matters because it is increasingly shaping how boards prioritize risk, allocate security budgets, and assign accountability. This divergence, highlighted in the World Economic Forum’s (WEF) Global Cybersecurity Outlook 2026, signals a meaningful shift in how cyber risk is being framed at the highest levels of organizations.
The WEF report is pushing cybersecurity beyond a purely technical discipline and into a CEO-level conversation about resilience, one that encompasses economic stability, business continuity, and trust alongside system defense.
For the CISOs out there, the challenge isn’t choosing between fraud and ransomware. It’s recognizing how executive definitions of cyber resilience are expanding and what that means for how risk is evaluated.

Why the WEF Frames Fraud as a Resilience Issue
In traditional cybersecurity practice, resilience has focused on systems: the ability to prevent intrusions, contain incidents, and restore operations after disruption. This framing naturally prioritizes threats like ransomware, outages, and infrastructure compromise.
The World Economic Forum approaches resilience differently. Its cyber resilience frameworks anchor resilience in business impact, defining it by an organization’s ability to minimize the effect of significant cyber events on core business goals.
Viewed through that lens, cyber-enabled fraud naturally becomes a resilience issue. Fraud doesn’t necessarily require downtime or destructive malware. It often occurs during normal operations, exploiting legitimate workflows and trusted relationships. But it still creates immediate and irreversible business impact.
From a resilience perspective, the question is no longer only whether systems survive an attack, but whether the organization preserves financial integrity and trust under pressure. The CEO and founder of a company dedicated to eliminating cyber-driven fraud, Shai Gabay, explains it this way:
“What stood out to me in the WEF report is that resilience is being defined by outcomes, not incidents. Once you take that view, it changes what counts as cyber risk—and what doesn’t always show up in traditional security metrics.”

Why CEOs and CISOs Rank Cyber Risks Differently
The WEF report attributes the difference in CEO and CISO priorities to role-based risk lenses, not disagreement.
CEOs tend to assess cyber risk through the lens of business and economic impact—how an incident affects continuity, financial exposure, and organizational trust. CISOs, by contrast, evaluate risk based on technical likelihood, threat activity, and operational disruption.
Both perspectives are valid. They reflect different responsibilities within the same organization. Fraud’s rise to the top of CEO concern does not diminish the importance of ransomware or infrastructure resilience. It highlights how executive-level definitions of cyber risk increasingly incorporate business outcomes alongside technical threats.
As conversations build around expanding the CISO’s reporting structure, influence, and presence in the boardroom, the role itself is evolving. With that evolution comes a clear expectation: CISOs must move beyond purely technical risk and take ownership of broader financial and operational resilience.
Where a CEO-Level Definition of Resilience Meets Enterprise Reality
Elevating fraud as a resilience concern raises a practical challenge: fraud does not belong to a single system or function.
A typical fraud scenario can span email and identity systems, vendor relationships, ERP platforms, and payment workflows—touching finance, security, procurement, and IT along the way. From an organizational standpoint, this makes fraud difficult to categorize using traditional security boundaries.
This isn’t a critique of existing resilience models. It’s an observation about scope. As resilience expands to include economic and trust-based outcomes, it inevitably intersects with parts of the organization that have not historically been treated as part of cyber risk.
“As the definition of resilience expands, so does the scope of cyber risk.”
What Enterprise Data Shows About Fraud as a Resilience Stressor
Trustmi’s research into socially engineered fraud provides a ground-level view of how these resilience challenges of cyber-enabled fraud appear in practice. In a survey of 525 finance and security leaders at large U.S. enterprises, fraud incidents were rarely isolated or incremental. They tended to be financially significant and spread across multiple systems.
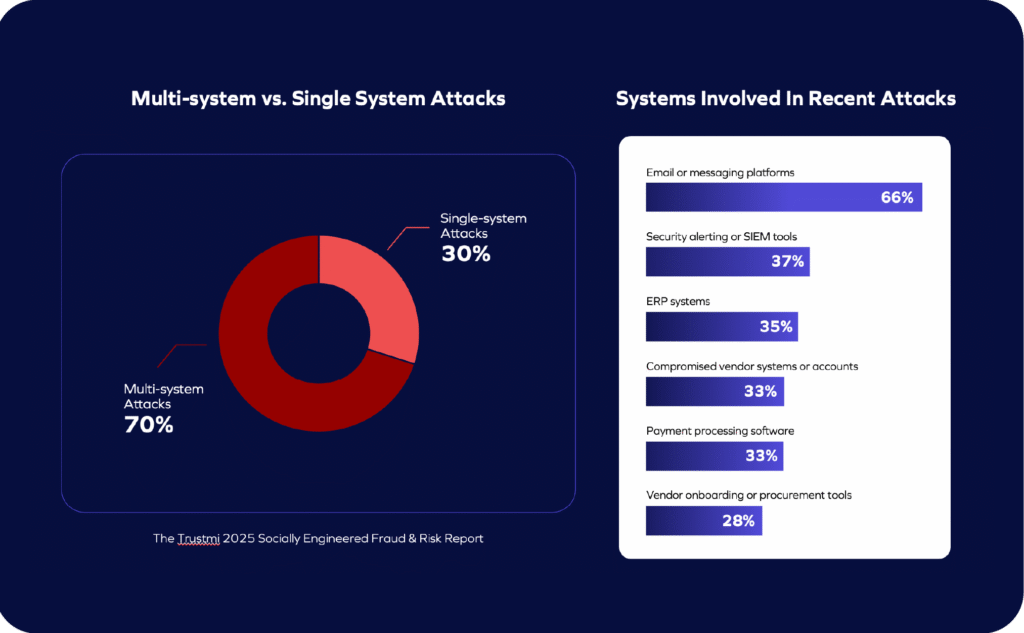
Seventy percent of reported fraud attempts spanned more than one system, frequently crossing platforms traditionally owned by both finance and security teams. Rather than reflecting the failure of a single control, these incidents unfolded as activity moved through connected workflows, tools, and approval processes.
A Live Demonstration of Multi-System Payment Fraud
Ethical hacker FreakyClown recreates a real-world fraud scenario
From a resilience standpoint, this pattern matters because it shows that fraud does not primarily test whether any one system or control works. It tests whether controls continue to hold as legitimate business processes interact across organizational boundaries.
And this is why resilience can no longer be defined by isolated controls or siloed signals—it has to be measured by what ultimately happens.
What This Research Helps Security Leaders Take Away
“Ransomware still matters. But resilience must expand to include cyber-driven fraud.”
For security leaders, the WEF report does not signal a need to abandon existing priorities like ransomware or infrastructure protection. These remain resilience critical.
What the report does suggest is an expanded view of resilience—one that increasingly accounts for financial integrity and trust as core outcomes of cybersecurity. In that context, fraud’s elevation reflects a broader purview, not a rejection of the operational focus security leaders have maintained for years.
Trustmi’s findings help explain why this shift can feel dissonant from a security perspective. Security teams often encounter the early technical signals associated with fraud, such as suspicious emails, anomalous access, or identity misuse, without direct visibility into how those signals ultimately translate into completed financial events. In other words, fraud doesn’t always show up like a typical security incident—there’s no malware, no outage, and often no alert. The full impact emerges across stages and functions, rather than within a single incident.
The Leadership Challenge Going Forward
The WEF has articulated a CEO-level view of cyber resilience grounded in business impact. The leadership challenge is how that definition translates into enterprise structures, measurement, and oversight, particularly for risks like fraud that span systems and functions.
As cyber-enabled fraud continues to evolve, understanding the specific attack patterns and organizational touchpoints involved will be critical. As a company devoted to eliminating social engineering that leads to cyber-enabled fraud, we’re going to continue to do more research. In the coming months, we’ll share deeper findings about fraud attack types and sequences that we’ve seen internally in 2025.
Want to see how fraud-related resilience stress actually plays out inside enterprises? You can watch ethical hacker, FreakyClown, demo the anatomy of an AI-driven payment fraud attack. Or you can download a free copy of the 2025 Socially Engineered Fraud & Risk Report.