Have you heard of FraudGPT?
Attackers have. And they’re already using it to generate vendor emails that look completely legitimate: it references real transactions, matches your company’s writing style, and bypasses the controls most organizations rely on to stop payment fraud.
This isn’t theoretical. In 2024, nearly 80 percent of organizations faced attempted or successful payment fraud. AI-powered tools like FraudGPT are accelerating the problem by eliminating the red flags finance and security teams have been trained to look for.
In this Trustmi guide, we explain what FraudGPT is, how attackers use it, and why traditional point solutions miss the patterns these AI-generated attacks create.
What Is FraudGPT?
FraudGPT is an AI-powered tool used to automate social engineering and payment fraud. By generating emails and payment requests based on real business context, it allows attackers to create messages that appear routine rather than suspicious—making detection by traditional controls far more difficult.
Unlike traditional phishing kits, FraudGPT doesn’t rely on generic templates or obvious errors. Its effectiveness comes from how well it blends into normal business workflows—producing messages that appear routine rather than suspicious.
Tools like FraudGPT dramatically lower the barrier to entry for sophisticated fraud. As ethical hacker FreakyClown put it: you no longer need nation-state resources to launch a complex attack. You can do it from a coffee shop—and finish before your drink gets cold.
How FraudGPT-Powered Payment Fraud Works
FraudGPT automates much of the research and writing that once took attackers weeks. Rather than launching a single obvious phishing attempt, attackers use it to coordinate activity across systems over time.
Here’s how these payment fraud attacks typically unfold:
- Gather business intelligence. Attackers collect information about vendors, invoices, payment timing, and approval workflows from public sources, compromised email accounts, or leaked documents.
- Generate realistic communication. FraudGPT uses this context to create emails that match your organization’s tone and reference real transactions—often starting with routine check-ins rather than immediate payment requests.
- Build credibility over time. Instead of rushing the attack, fraudsters maintain ongoing conversations, responding naturally to questions and clarifications to establish trust.
- Introduce urgency at the right moment. Once credibility is established, attackers introduce urgency—such as bank detail changes, delayed payments, or time-sensitive issues tied to real business operations.
- Divert the payment. By the time the final request is made, it appears consistent with prior communication and passes through normal approval workflows.
To witness what this process looks like from start to finish, watch a demo of modern payment fraud with ethical hacker, FreakyClown.
Key Risks Posed by FraudGPT
FraudGPT introduces a set of risks that traditional fraud controls were not designed to handle. These risks aren’t limited to better-written emails—they reflect a fundamental shift in how payment fraud is executed.
Eliminates Traditional Fraud Detection Signals
Spelling errors, awkward phrasing, and generic templates once helped teams spot fraud attempts. However, FraudGPT removes these warning signs entirely. Every email reads authentically and references accurate business details.
When fraudulent messages look exactly like the legitimate vendor communications finance teams process every day, manual review becomes unreliable.
Bypasses Email Security Filters Completely
FraudGPT-generated messages contain no malicious links, no attachments, and no known phishing indicators. They are simply clean, professional text requesting what appears to be a routine business action.
Because traditional email security tools are optimized to detect malware and phishing infrastructure—not social engineering that unfolds over time—these messages often pass through without issue.
Enables Hyper-Personalized Attacks
FraudGPT allows attackers to tailor messages using publicly available information and internal context gathered from compromised accounts. Each email can reference specific vendors, invoices, payment amounts, or approval workflows.
This means attackers can run hundreds of highly personalized campaigns simultaneously—making mass fraud feel like one-to-one communication and defeating pattern-based detection.
Adapts in Real Time to Bypass Verification
When a finance team questions a request, attackers can feed the response directly into FraudGPT. The AI generates convincing follow-up messages that maintain tone, context, and identity consistency.
This makes traditional verification steps—such as email back-and-forth or ad hoc confirmation—far less effective, as the attacker can respond instantly and convincingly.
Exploits Real Business Urgency and Authority
FraudGPT is particularly effective at generating messages that mimic operational pressure: audit deadlines, vendor issues, executive travel, contract risks, or quarter-end timing.
By impersonating the right vendor or executive at the right moment, attackers increase the likelihood that employees act quickly—before fully questioning the request.
Makes Advanced Payment Fraud Accessible to Anyone
With low-cost subscriptions and no technical barrier to entry, FraudGPT makes sophisticated fraud techniques available to virtually anyone.
What once required skilled social engineering, deep research, and careful writing is now automated—dramatically expanding the number of attackers capable of launching convincing payment fraud attacks.
Why Point Solutions Miss FraudGPT Attacks
Email security tools scan for malware and phishing patterns. Payment verification platforms check bank accounts. ERP systems log approvals. Each tool protects one piece of the payment process.
FraudGPT-powered attacks don’t fail at a single checkpoint. They unfold gradually across systems, workflows, and approvals—often over days or weeks. As a result, defenses that only evaluate one moment in the payment process are inherently limited.
Stopping these attacks requires visibility across the entire payment lifecycle, not isolated controls that operate independently.
Effective protection against FraudGPT-powered fraud requires several capabilities working together:
1. Behavioral AI Across the Entire Payment Lifecycle
Effective defenses use behavioral AI to understand how your finance operations normally function across every stage of the payment lifecycle. This includes patterns such as:
- How vendors typically communicate
- Normal invoice amounts and payment timing
- Usual approvers and workflow routes
- Standard bank detail and contact information changes
When activity deviates from these patterns, risk can be identified—even if each individual step appears legitimate in isolation.

2. Deep ERP and Financial System Integration
Because many FraudGPT attacks rely on subtle changes inside finance systems, effective defenses must monitor how vendor records, approvals, and payment data evolve over time.
This allows teams to identify and flag risk signals, including:
- Unusual workflow routes or skipped approval steps
- Sudden vendor or bank detail changes
- Invoice mismatches across systems
- Approvals initiated by unexpected users or devices
By tracking how these signals change across systems, patterns can be surfaced long before the payment is executed.
3. Cross-Channel Communication Analysis
Effective defenses analyze activity across every channel involved in the payment workflow, including:
- ERP logs
- Vendor portals
- Payment approvals
- Changes made inside finance systems.
By connecting these signals, teams can surface inconsistencies—such as emails that appear clean but conflict with ERP activity, bank change requests that don’t align with vendor behavior, or approvals initiated by unexpected users or devices.
4. Document and Metadata Integrity Analysis
Attackers use FraudGPT to create invoices and documents that look authentic. They may copy vendor formatting, use the correct payment terms, and include accurate project details. Traditional email security doesn’t catch these alterations.
Effective defenses take a deeper dive by examining the structure and history behind every file. This includes analyzing metadata and document origins to identify any changes that don’t match normal vendor behavior, such as:
- Invoices created or modified with unusual software
- Metadata showing edits made after the document was sent
- Bank details inputted in ways not consistent with past versions
This makes it possible to catch tampered documents that pass surface-level checks.
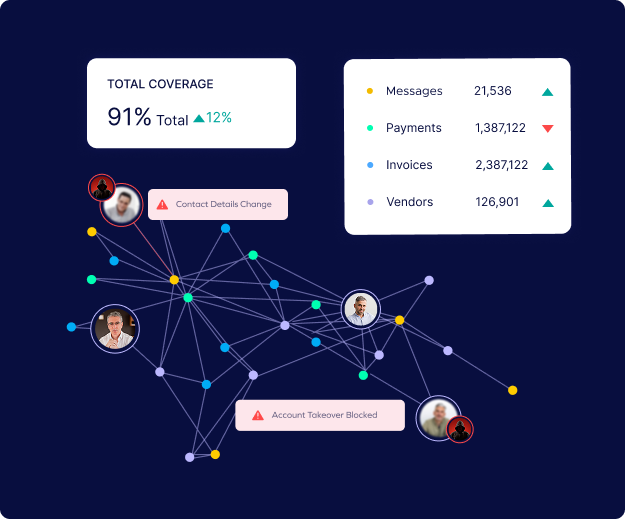
5. Real-Time Payment Interception Before Money Moves
Even when attackers get past email security and convince an employee to approve a change, effective defenses must be able to intervene before funds leave the organization.
This includes monitoring every step of the payment process in real-time and stopping transactions that break established behavioral patterns, such as:
- Payments sent to newly added or modified bank accounts
- Approval flows that skip required steps or use unusual timing
- Invoice amounts or vendor details that do not match historical records
By stopping payments mid-process, teams gain time to investigate and confirm legitimacy—preventing losses even when a FraudGPT-powered scam looks perfect at every earlier stage.
Strengthen Your Payment Protection Against FraudGPT With Trustmi
FraudGPT and other AI-driven tools have made payment fraud faster, more convincing, and far harder to detect. As attackers use automation to bypass traditional controls, businesses need protection that looks beyond email and identifies anomalies wherever they occur.
Trustmi brings these capabilities together in a single platform designed to protect the entire payment lifecycle.
By analyzing behavior across vendors, communication channels, ERP systems, and payment execution, Trustmi helps finance and security teams detect coordinated fraud patterns that isolated controls miss—allowing organizations to intervene before fraudulent payments are completed.
Ready to secure your payment operations with confidence? Request a Trustmi demo and see how we can help.